Coordinated Response
Services and tools for incident response management
What Else Does NIST Say?
The National Institute of Standards and Technology (NIST) released The Computer Security Incident Handling Guide, SP 800-61 Revision 2, in August, 2012.
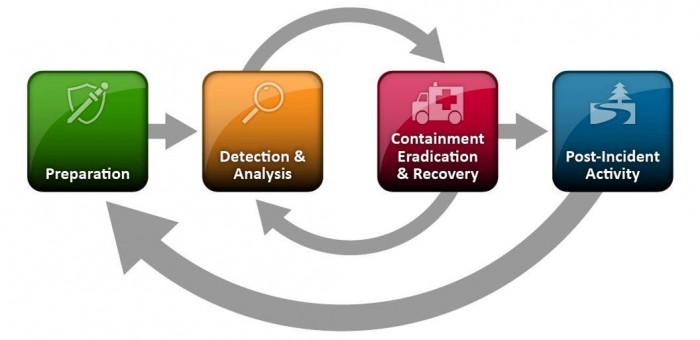
The guide puts incident handling activities in the context of the above diagram. The table below provides the first level of detail.
| Preparation | Detection & Analysis | Containment, Eradication, & Recovery | Post-Incident Activity |
|---|---|---|---|
|
|
|
|
The above activities represent a useful checklist for evaluating an incident response plan as well as incident handling in action.
Of course, recognize that the response to an incident is fluid, often with unclear boundaries. Containment may start in the early stages of analysis. Prioritization may change and notification may continue throughout the incident. But, the insight provided by the NIST publication goes beyond Federal agencies.


Leave A Comment
You must be logged in to post a comment.