Coordinated Response
Services and tools for incident response management
Incident Response Plan
Do You Have a Cybersecurity Incident Response Plan?
Does it Address Insider Threat?
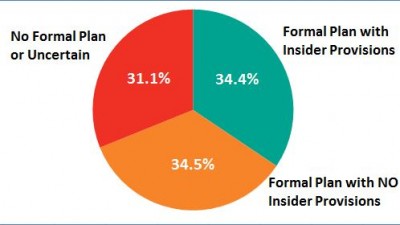
The SANS Institute recently published a study, Insider Threats and the Need for a Fast and Directed Response. The study shared the results of a survey with over 700 respondents from a wide range of organizations covering the private and public sectors.
Two thirds of the respondents had a formal incident response plan. That’s the good news. Still one third had no plan or were uncertain if there was plan. But, that means two thirds had no provisions for dealing with an insider incident; and nearly half of all organizations are likely to experience an insider incident in the next 12 months according to CERT/CC. Further, most organizations found insider incidents more damaging than incidents instigated by intruders.
The study was sponsored by SpectorSoft, a leader in activity monitoring software. To get a copy or to attend a webinar with Dr. Eric Cole, the study’s author visit: SpectorSoft – SANS Survey Report.
To get help with your response plan visit Coordinated Response.
To learn more about insider threats, get a copy of The Common Sense Guide to Mitigating Insider Threat from The Software Engineering Institute at Carnegie Mellon University.
Coordinated Response
Let us help you with a response plan review that considers insider threats. Addressing insider threats in your incident response plan is an industry best practice.
For more information on Insider Threat consider the following articles:
Cyber Effectiveness – Board Engagement and an Audit Plan
This may be a litmus test.
In an article on Banking Exchange, Cybersecurity top of mind for auditors, a survey with over 800 participants showed a strong correlation between 2 factors — board engagement and a good audit plan – and an effective cybersecurity program.
The article shared the results of a survey by Protiviti. The survey presented the following as the top risks identified by the respondents:
- Data security / company information,
- Brand / reputational damage,
- Regulatory and compliance violations tied with
- Data leakage, and
- Viruses and malware.
Governance
Organizations reporting higher confidence in the cybersecurity program also reported active board engagement and an effective audit program — Governance.
Coordinated Response
Most audit programs include a review of the incident response plan and a review/audit of incidents recorded in the past year. To help with a successful audit, let us help you with a succesful response plan review.
Five Stages of Data Breach Grief
Ricky Link in an article on the Dark Reading web site suggests that customers aren’t the only victims of a data breach.
Mr. Link suggests that the organization and even the security team go through the 5 stages of grief identified by Elizabeth Kubler-Ross in her book On Death and Dying:
Denial, Anger, Bargaining, Depression, and Acceptance.
Data Breach Denial
There was no data breach, was there? It wasn’t that big?
Anger
How the [expletive deleted] did this happen?
Bargaining
How about a second chance? This won’t happen again.
Data Breach Depression
What are we going to do now? How will this affect our business?
Acceptance
Once a data breach is an accepted fact, the post mortem (to continue with the death metaphor) can begin.
Coal Fire
Ricky Link is the Managing Director for Coalfire in the Dallas, Texas office. His article provides valuable insight when dealing with a data breach. He also provides a table with the 17 major data breaches in 2014 with over 313 million records exposed across the 17 breaches.
Coordinated Response
We don’t recommend reflecting the 5 stages of grief in your incident response plan, but it makes sense to recognize the stages during plan development. What actions advance the response beyond these gates?
Let us help you with a cybersecurity incident response plan review so your plan moves incidents rapidly to an optimal resolution.
Ubiquitous Limitations with Incident Response
A data forensic expert, often involved with response to a cybersecurity incident, identified 9 limitations he repeatedly experiences with organizations when he participates in their incident response.
These 9 weaknesses or limitations hinder incident response efforts – costing time, money, and potentially the organization’s reputation.
Addressing the 9 limitations makes a good set of New Year’s resolutions. These resolutions form the outline of a good plan for incremental improvements throughout the year to come.
The table below addresses these limitations in the form of an incremental plan. It’s divided into 3 phases: Phase I – Lay a foundation; execute tasks that would result in time savings if an incident occurs; Phase II – Pluck low hanging fruit; execute tasks that would immediately improve your security profile and reduce the likelihood of an incident; and Phase III – Plan and raise your security profile; add procedures and tools to enhance your cybersecurity incident response capabilities.
| Phase I | Phase II | Phase III |
|---|---|---|
| Inventory and Inventory Control | Legacy Equipment and Software – Low Hanging Fruit | Legacy Equipment and Software – Incremental Reduction |
Review or Develop the Inventory of IT Assets:
|
Through the inventory process identify low hanging fruit – remove components that can be retired or replaced easily. Develop a plan to remove remaining items through a phased approach. Include a budget and a return on the necessary investment. Tie investment to risk reduction and value to the organization. | Implement a cost / benefit approach to incrementally eliminate legacy components. Include remaining legacy components in a risk register; plan to address these components next year. |
| Change Control | Harden DMZs | Network Visibility |
| Along with inventory control, establish and follow policies and procedures that control changes to the IT infrastructure. Limit end users’ ability to install software. Limit the ability to modify hardware and software configurations. Audit changes. |
Too often, DMZs look good on paper, but have been degraded with time. As a result of the inventory process, review the DMZ, close gaps, harden it, and update the documentation. |
Improve the network inventory – know the scope of the network and its components. Improve network monitoring tools. |
| Administrative Accounts | Staff Capabilities and Requirements | Incident Response Capabilities |
| Identify and limit administrative accounts. Employ least privilege and separation of privilege. | Review staff capabilities and requirements. Develop plan to fill gaps through hiring, training, realigning. | Review the risk assessment and incident response plan. Identify gaps and a plan to fill them. |
| Users – Policy | Users – Education and Training | Users – Monitoring |
| Review / establish policies including acceptable use of IT assets and privacy. Address mobile devices especially “bring your own devices” (BYOD). | Educate users on the policies; establish their acceptance of the policies. Develop and implement awareness training. | Establish tools to monitor users especially users with elevated privilege. |
A Coordinated Response to Cybersecurity
Phase I might include an incident response plan review. The response plan includes input from the following activities: inventory, privilege accounts, and staffing requirements. It provides input to the staffing requirements, legacy equipment, and incident response capabilities. So, if you resolve to improve your cybersecurity posture in the coming year, Coordinated Response can help you get started with a response plan review.
Standards for Incident Handling are like English
The English language is spoken with different accents and different vocabularies while still saying the same thing.
The standards for Incident Handling use different vocabularies, but they also say the same thing.
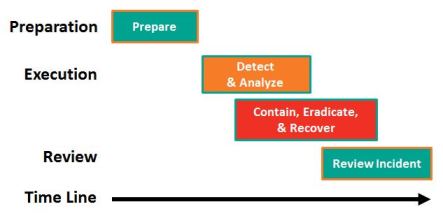
The table below compares the language used by 4 authorities to describe the incident handling phases. The authorities employ 4, 5, or 6 phases.
| Phase | NIST SP 800-61 | ISO 27035 | SANS | ISACA |
|---|---|---|---|---|
| Before | Prepare | Planning & Preparation | Preparation | Preparation |
| During | Detect & Analyze | Identify & Report | Identification | Detect, Triage, & Investigation |
| Contain, Eradicate, & Recover | Assess | Containment | Containment, Tracking, Analysis, & Recover | |
| Respond | Eradication | |||
| Recovery | ||||
| After | Review Incident | Learn | Lessons Learned | Post Incident Assessment |
| Incident Closure | ||||
| Total | 4 Phases | 5 Phases | 6 Phases | 5 Phases |
National Institute of Standards and Technology
NIST SP 800-61 Rev 2 Computer Security Incident Handling Guide, 2012.
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
International Standards Organization
ISO/IEC 27035:2011 Information technology — Security techniques — Information security incident management, 2011.
http://www.iso.org/iso/catalogue_detail?csnumber=44379
SANS Institute
The Incident Handler’s Handbook, 2011.
http://www.sans.org/reading-room/whitepapers/incident/incident-handlers-handbook-33901
ISACA
Incident Management and Response, 2012.
http://www.isaca.org/Knowledge-Center/Research/ResearchDeliverables/Pages/Incident-Management-and-Response.aspx
Coordinated Response
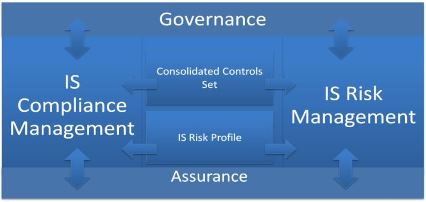
The Response Management Framework aligns well with all of these approaches. Let us apply the framework in a response plan review.
NIST Guide to Conducting Risk Assessments
NIST Special Publication 800-30 identifies Respond as 1 of 4 risk management processes. In order to properly complete the Risk Assessment, an incident Response Plan needs to be considered in parallel.
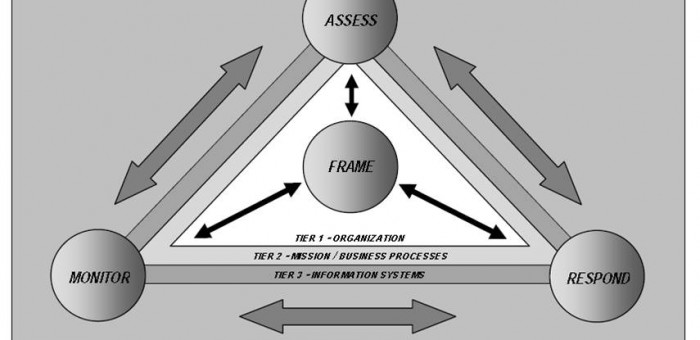
Four Risk Management Processes
Respond is 1 of the 4 Risk Management Processes identified in the Guide. Respond includes pre-emptive security controls to mitigate risk, but it also includes Incident Response Planning, Management, and Execution. Respond receives input from and provides input to the other 3 processes: Frame, Assess. and Monitor.
The Assess process has a number of key dependencies on the approach to incident response. I will look at these in my next post.
Coordinated Response
Coordinated Response can work with you to align your response plan with your Risk Assessment. Let us help you with a response plan review that considers your information security risk assessment.
For more information on how we see risk assessment linked with incident response refer to an earlier highlight: https://coordinatedresponse.com/risk-assessment-and-incident-response/.
NOTE: The graphic above is from NIST SP 800-39 Managing Information Security Risk page 32. It is similar to the graphic in SP 800-30 Rev 1 on page 4, but in SP 800-39 the graphic provides more information. Specifically the 3 organizational tiers are identified.
For access to NIST Special Publications: http://csrc.nist.gov/publications/PubsSPs.html, SP 800-30 Rev 1, “Guide for Conducting Risk Assessments,” Sep. 2012.
FIRST Recommended Incident Categories
Categorizing incidents helps establish a consistent and effective Incident Response Plan.
FIRST, the Forum for Incident Response and Security Teams, provides great resources for developing an Incident Response Plan through the FIRST Web Site.
One web page provides guidance on Incident Categories that we use as a baseline for the initial categories in our Response Management Framework. The guidance stresses Consistent Case Classification/Categorization to help achieve key objectives:
- Provide accurate reporting to management;
- Insure proper case handling; and
- Form the basis for Service Level Agreements (SLAs) between the CSIRT and other departments.
Consistent Categories also address the following:
- Effectively communicate the scope of CSIRT responsibility to executives and constituents;
- Inform the development of appropriate response actions; and
- Insure consistent case handling.
Like incidents are likely to require like actions. This helps in the development of the response plan and its effective execution.
Incident Categories
The following table presents the FIRST categories on the left and the categories as adapted for the Coordinated Response Management Framework on the right.
| Categories Proposed by FIRST | Comments / Suggestions |
| Denial of Service – DoS or DDoS attack; attrition. | Every organization experiences DoS at some point. |
| Forensics – any forensic work performed by the CSIRT. | Forensics may be one of many services performed by the CSIRT. CSIRT Services might make a better category with Forensic Services as a specific service type. |
| Compromised Information – attempted or successful destruction, corruption or disclosure of sensitive information. | |
| Compromised Asset – host, network device, application, or user account. | The assets mentioned serve as examples. Mobile devices, any computers: desktop, laptop, notepad, might also be compromised. Lost or stolen equipment might be considered compromised, but perhaps this should be an additional category. |
| Unlawful Activity – theft, fraud, human safety, or child porn. | Any number of incident categories might result in illegal action. Perhaps, unlawful activity might better serve as an impact category. In most cases of unlawful activity, this is not known at the incident response outset. |
| Internal Hacking (inactive or active) – recon or suspicious activity with internal origins. | |
| External Hacking (inactive or active) – recon or suspicious activity with external origins. | |
| Malware – a virus or worm typically affecting multiple corporate devices. | |
| Email – spoofed email, SPAM, etc | |
| Consulting – security consulting unrelated to a specific incident. | This is another example of a CSIRT Service. |
| Policy Violations – inappropriate use, sharing offensive material, or unauthorized access. | As with unlawful activity, policy violation may be a measure of incident impact. |
The FIRST categories have been re-ordered to more readily reflect the mapping to the Coordinated Response proposed categories.
The categories for Compromised Information and Assets are augmented with a category for Loss or Theft of Equipment. These 3 categories share common actions, but there are distinct actions as well. Because each of these categories represent a number of distinct incident types they are best left as separate categories.
DDoS, Email, and External hacking are better treated as incident types and combined under a category for External Incidents. Attacks originating outside an organization are likely to involve a set of external resources from the Internet Service Provider (ISP) to external reporting authorities.
Internal Incidents very likely involve Human Resources and Legal. Internal Hacking is an incident type. Policy Violation may not represent an incident type, but a level of impact.
Unlawful activity is a measure of the legal impact of the incident. External or Internal hacking might rise the level of Unlawful Activity. Or not.
Finally, CSIRT Services might include Forensics, Consulting, and other services. This reflects an important category. The CSIRT might analyze and summarize Threat Intelligence and provide a synopsis to internal audiences.
Impact Levels
The FIRST guidance on categories also introduces Sensitivity and Criticality. Sensitivity applies to the nature of the incident. Denial of Service might rate S3 – Not Sensitive or Low Sensitivity. Policy Violations might rate S2 – Sensitive or Medium Sensitivity. A Forensics Request or Compromised Information might rate S1 – Extremely Sensitive or High Sensitivity. Criticality is measured in a similar way.
The Response Management Framework considers Sensitivity and Criticality as impact areas with associated impact levels. A future highlight on Impact Assessment will include more on FIRST guidance.
Other Categories
Other organizations propose categories for use in incident response planning – organizations including US-CERT at the Department of Homeland Security, the Office of Management and Budget (OMB), and the National Institute of Science and Technology.
A future highlight will address incident categories advanced by these organizations and how the proposed categories relate to other categories.
Coordinated Response
Recognizing an incident and its category aligns actions with desired outcomes. Categories need to reflect an organization, its response team, and its security controls. The categories presented here are offered as a starting point and a proven best practice.
Refer to our Response Management Framework for added insight.
Let us help you with a response plan review that considers your information security risk assessment.
US-CERT: Combating Insider Threat
A High-Level View to Help Inform Senior Management
The US-CERT Web Site offers a 5 page paper on “Combating Insider Threat”.
This well written document summarizes the nature of the threat and an approach to detect and deter malicious insider activity. The paper is valuable for 2 reasons:
- It is the right document from the right source to inform executive leadership and board members on the importance of addressing insider threats; and
- It provides a great set of references – good resources for informing an effective program to address insider threat.
First, Consider the Insider
The paper describes the characteristics of “an Insider at Risk of Becoming a Threat” – characteristics recognized by executive leadership. The characteristics of a troubled employee – for example, rebellious or passive / aggressive activity; low tolerance for criticism – may lead to difficulties in a number of ways including a cyber incident.
The paper then identifies “Behavioral Indicators of Malicious Threat Activity” – indicators including an employee interest in areas outside the scope of their responsibility or an employee accessing the network at odd hours or while on vacation or sick leave. Monitoring employee activity is an important part of identifying potential threats.
Then, Detect and Deter
The paper identifies technologies for detection and deterrence. Technologies include data-centric security: data/file encryption, data access control /monitoring, and data loss prevention; intrusion detection / prevention systems; and enterprise identity / access management. The paper helps make the case for the use of the technologies.
The paper also describes the social science behind deterrence strategies – strategies equally applicable to fraud, cybersecurity, and other bad behavior.
Finally, References and Resources
The paper cites 32 references, 29 with online links. I strongly recommend downloading the paper and perusing the links for those that might enhance your insider threat program.
It starts with a link to the Carnegie Mellon CERT Insider Threat web site.
Coordinated Response
This paper focuses on how to Deter and Detect insider threats. We focus on the Coordinated Response to an insider incident. We can help make the case to executive leadership on building an effective insider threat program.
Let us help you with a response plan review that considers your information security risk assessment.
Insider Threat – Webinar
Insider Threats: Learn How to Find them Early and Fix Them Fast!
Your organization has a 50% likelihood of experiencing an insider incident despite deep investments in IT security. Insider threats include fraud, theft of intellectual property, data breaches and leaks, or malicious damage to IT resources. Most organizations that experienced an insider incident indicate it was more damaging than incidents involving hackers. You need the right plan and the right tools to detect, respond and recover from an insider incident.
Join Us on June 5th at 2 PM EDT
Join Mike Tierney, the COO of SpectorSoft and Jim Meyer, Managing Director at Coordinated Response on June 5 at 2 PM EDT for this 60 minute webinar hosted by Dark Reading.
Attend this webinar to learn:
- Effective approaches to detect and address insider threats.
- Research and resources from industry experts to help you prepare and react.
- Best practices from years of hands-on experience and client engagements.
Verizon data breach investigations report indicates that any breach, insider or otherwise, if found early is 80% less likely to result in damage. Register for this webinar and learn how to find insider threats early and fix them fast.
Watch this webinar on YouTube
To see a replay of this webinar go to YouTube.
What to Do After a Data Breach
Eight Best Practices to Effectively Deal with a Data Breach
On the CIO Insight web site Karen Frenkel posted a slide deck that identifies 8 best practice for dealing with a data breach. The practices identified align nicely with the elements Response Management Framework.
I recommend the slide deck as a good device for a review and a discussion with your executive team.
Eight Best Practices for a Data Breach Response
- Prepare and Practice to Make Perfect.
- Don’t Panic!
- Move Quickly, but Stay Patient.
- Don’t Go It Alone.
- Assemble the Right Team.
- Get Legal Advice.
- Someone Needs to Talk.
- Identify Lessons Learned.
Coordinated Response
So apply these best practice as you evaluate and improve your incident response plan. Refer to our Response Management Framework for added insight.
Let us help you with a response plan review that considers your risk of a Data Breach.
A Note of Appreciation
Thanks to Jeff Mathis and the LinkedIN Cyber Resilient Community Dialog for bringing this to my attention.