Coordinated Response
Services and tools for incident response management
Federated Cybersecurity: A Hybrid Approach to Safety
I attended the CSO Perspectives event in Alexandria, Virginia on March 21st. This event was produced by CSO Magazine and CSO Online. Publisher Bob Bragdon was the host and moderator. During the course of the day, there was an extensive discussion of the Federal Government’s role in Cybersecurity.
Over lunch, with Bob and a number of others, I suggested we need a federated approach to cybersecurity.
Consider highway safety for a moment and all the factors that make it safe to drive:
- Highways are built to a standard of safety. Interstate highways meet Federal standards. The standard defines safe lane widths, median strips, shoulders, guard rails when necessary, on and off ramps and more.
- State and local laws dictate speed limits.
- State and local police enforce the laws.
- Federal regulations direct automotive manufacturers to build safe cars with seat belts and air bags, signal lights, brake lights, and more.
- Automotive manufacturers add crash zones and other details competing for the moniker of safest.
- You and I are required to get a driver’s license by passing a written test and a driving test (though I confess it’s been a few decades since I last took the test).
- Young drivers need to meet a higher standards in most states to get their drivers permit.
- Our insurance companies encourage us to drive safely with threat of higher premiums when we don’t.
- Of course, there are incident response services: from emergency response to AAA.
This federated approach to safety and security is needed on the information highway (now there is a dated term). We expect hardware and software manufacturers to build safer products. But, we need to be trained to use them properly and not to turn off safety features or, in some cases, we need to be trained to turn them on. The network service providers and internet service providers need to build safer “highways”. We still need government regulations and enforcement.
How do we protect against malicious drivers? This is a metaphor worth exploring.
What Does NIST Say About Incident Response?
The National Institute of Standards and Technology (NIST) produced a list of Security Controls for Federal Information Systems. Incident Response is one of the controls.
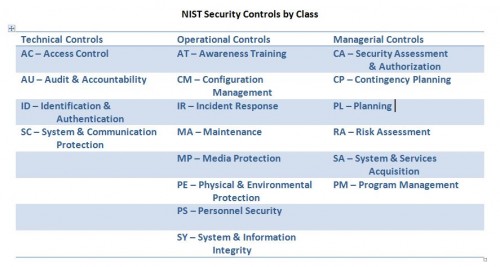
In Special Publication 800-53, revision 3 NIST included Incident Response as 1 of 18 families of security controls. For the complete list see the end of this item. Much of the material is useful beyond the Federal government.
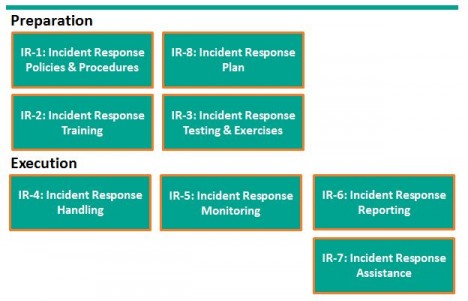
First, NIST provides a useful framework for considering Incident Response (IR). Please don’t let the control numbers confuse things. I started with preparation, but NIST considers IR Planning as IR-8.
Incident Response preparation starts with Policies and Procedures and the preparation of an incident response plan. With the plan in hand, train users how to recognize and report incidents, train the response team how to organize and react. For some incidents, actually testing the plan with field exercises may be needed.
Incident response execution includes handling, monitoring, reporting, and possibly additional assistance from specialists. NIST suggests each organization consider these controls and determine when or whether they apply.
In SP800-53, Revision 4 Draft, two additional controls were identified: IR-9 Information Spoilage Response and IR-10 Integrated Information Security Cell. The first addresses the additional needs for damaged or leaked information. The latter describes the organization of a specialized element of the Incident Response Team.
While the Incident Response Plan is just one of 8 controls, it touches all the other controls. NIST declares a good Incident Response Plan:
- Provides road map for implementing incident response capability.
- Describes the structure and organization of the incident response capability.
- Provides a high-level approach for how the incident response capability that fits into the overall organization.
- Meets the unique requirements of the organization, which relate to mission, size, structure, and functions.
- Identifies reportable incidents.
- Provides metrics for measuring the incident response capability within the organization.
- Defines the resources and management support needed to effectively maintain and mature an incident response capability.
- Is reviewed and approved at an appropriate level.
I heartily agree with NIST’s declaration.
NIST Security Controls
Here is the complete list of security control families identified in SP 800-53 and organized by the three control classes: Technical, Operational, and Managerial.