Coordinated Response
Services and tools for incident response management
Insider Threats and Incident Response
Insider Threats place added requirements on an incident response plan.
In December 2012, The CERT/CC Insider Threat Center published the Common Sense Guide to Mitigating Insider Threats, 4th Edition, CMU/SEI-2012-TR-012. The guide uses extensive research to examine the nature of insider threats and their probability. It is an excellent resource.
This is the first in a series of notes on insider threats – the first note examines the guide and the next considers the impact on incident response planning and handling.
The response to insider threats often involves a wide range of organizational staff.
“Insider threats are influenced by a combination of technical, behavioral, and organizational issues” (from the Executive Summary). As a result, management,human resources (HR), legal counsel, and physical security may be involved in the response along with the Information Technology (IT) and Information Assurance (IA) departments.
Of course, this aligns with the Core and Extended Response Team in the Response Management Framework.
Insiders reflect a range of company relationships and behaviors.
The range includes:
- The traditional threat posed by current or former employees;
- Collusion with outsiders – employees recruited or coerced by competitors or organized crime;
- Business partners – suppliers, contractors, or distribution channels;
- Mergers and acquisitions introducing new, unknown insiders; and
- Cultural issues – both national and corporate – introducing tensions.
Each of these may require specialized incident actions as part of the response.
The 2011 CyberSecurity Watch Survey informs the guide.
The CyberSecurity Watch Survey provides the following statistics:
- 43% of respondents experienced a malicious, deliberate insider incident in the past 12 months.
- 23% of identified perpetrators were insiders – 1 in 4 incidents perpetrated by insiders.
- 46% of respondents felt insider incidents caused more damage than incidents perpetrated by outsiders.
This annual survey is sponsored by U.S. Secret Service, CERT Insider Threat Center, Deloitte, and CSO Magazine.
The 2012 CyberSecurity Watch Survey provides additional support.
The following chart suggests that all organizations – large and small – have close to a 50/50 chance of experiencing an insider incident in any given year. Or every 2 years give or take a month an insider incident will occur. NOTE: there were 479 respondents, 1/3 were organizations with 5,000 employees or more, 2/5 were organizations with less than 500. This suggests a representative survey.
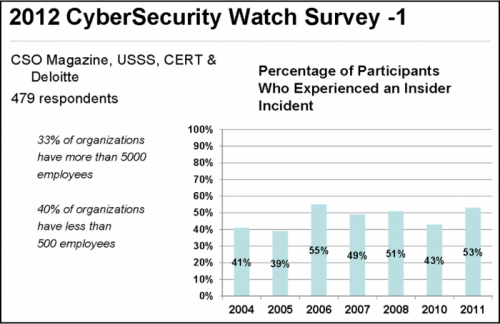 |
||
| The 2012 Survey was retrieved from a Google search for “2012 CyberSecurity Watch”. |
The guide recommends 19 practices to mitigate insider threats.
The guide recommends 19 practices for mitigating Insider Threats (See the table at the end of this article). Many of these are well known security controls, but they are presented through the lens of the insider threat. For each practice, the guide (1) defines the protective measure; (2) identifies challenges; (3) provides case studies; (4) identifies quick wins applicable to all organizations; (5) identifies additional quick wins for large organizations; and (6) maps the recommend practices to NIST, CERT, and ISO standards.
Coordinated Response – Review your plan.
We can work with you to incorporate or improve how your response plan addresses insider incidents.
The 19 Practices for Mitigating Insider Threats.
Emphasized practices have a direct bearing on incident response planning and management.
| 1 | Include insider threats in an enterprise-wide risk assessment. | 11 | Institutionalize system change controls. |
| 2 | Clearly document and consistently enforce policies and controls. | 12 | Log, monitor, and audit insider actions with log correlation or SIEM system. |
| 3 | Incorporate insider threat security training for all employees. | 13 | Monitor and control remote access including mobile devices. |
| 4 | Beginning with the hiring process, monitor suspicious or disruptive behavior. | 14 | Develop a comprehensive employee termination procedure. |
| 5 | Anticipate and manage negative issues in the work environment. | 15 | Implement secure backup and recover processes. |
| 6 | Know your assets. | 16 | Develop a formalized insider threat program. |
| 7 | Implement strict password and account management policies and practices. | 17 | Establish a normal network behavior baseline. |
| 8 | Enforce separation of duties and least privilege. | 18 | Be especially vigilant regarding social media. |
| 9 | Define explicit security agreements for any cloud services – address access restrictions and monitoring capabilities. | 19 | Close the doors to unauthorized data exfiltration. |
| 10 | Institute access controls and monitoring on privileged users. |
From the SEI/CMU Common Sense Guide for Mitigating Insider Threats, 4th Edition.

