Coordinated Response
Services and tools for incident response management
Does SIEM Meet Your Incident Response Needs?
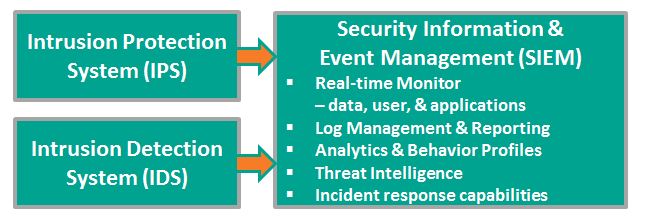
Security Information & Event Management (SIEM) systems provide real-time monitoring and advanced analytics and generate automatic alerts for potentially adverse events.
Most SIEM vendors from HP and IBM to LogRythm and LogLogics offer tools that support incident response, but in the words of one research organization the response is IT-focused and tightly coupled to the SIEM. The enterprise is not involved. Artifacts are limited to SIEM records. Incidents derived from outside the SIEM – help desk tickets, third party alerts, etc. – are not tracked at all.
There is a need to manage incidents at an enterprise-level. In addition to IT, there is involvement and support from:
- Risk Management Operations
- Corporate Counsel and outside legal counsel
- Public Affairs, Public Relations, and/or Media Relations
- Executive Leaderships
- Security Operations – Physical Security and Facilities Management
- Third party experts – IT, Forensics, Cybersecurity, Legal, etc.
SIEM vendors provide no interface supporting these enterprise actors. The researchers suggest connecting with an enterprise process automation platform, for example, Microsoft (TM) SharePoint, a platform that provides:
- Content and records management for Incident Documentation and Evidence
- Process automation with Alerts, Notifications, Approvals, and Assignments
- Change management records and audit trails
Coordinated Response embraces the SIEM response capability, but extends it to the Enterprise level.
What Else Does NIST Say?
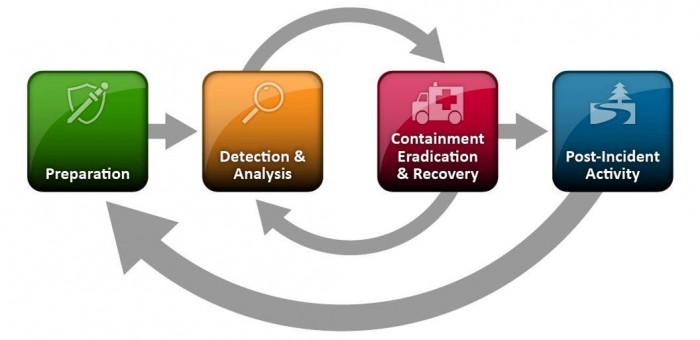
The National Institute of Standards and Technology (NIST) released The Computer Security Incident Handling Guide, SP 800-61 Revision 2, in August, 2012.
The guide puts incident handling activities in the context of the above diagram. The table below provides the first level of detail.
| Preparation | Detection & Analysis | Containment, Eradication, & Recovery | Post-Incident Activity |
|---|---|---|---|
|
|
|
|
The above activities represent a useful checklist for evaluating an incident response plan as well as incident handling in action.
Of course, recognize that the response to an incident is fluid, often with unclear boundaries. Containment may start in the early stages of analysis. Prioritization may change and notification may continue throughout the incident. But, the insight provided by the NIST publication goes beyond Federal agencies.