Coordinated Response
Services and tools for incident response management
Insider Threat
CFOs Need to Focus on Cybersecurity Risk
Incident Response – Executive Awareness.
An article on CFO.COM by Jeffrey Burchill, identifies cybersecurity risks associated with suppliers, service providers, and insiders.
Mr. Burchill, a CFO in the insurance industry, makes the case for CFO involvement in reviewing suppliers and service providers for potential cybersecurity vulnerabilities and risks. He raises a warning about the potential threat posed by insiders, malicious or inadvertent but still a threat.
Clearly, this article speaks to the CFO.
The article is available at: http://ww2.cfo.com/cyber-security-technology/2015/07/cfos-cybersecurity-risk-like-iceberg/
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
US-CERT: Combating Insider Threat
A High-Level View to Help Inform Senior Management
The US-CERT Web Site offers a 5 page paper on “Combating Insider Threat”.
This well written document summarizes the nature of the threat and an approach to detect and deter malicious insider activity. The paper is valuable for 2 reasons:
- It is the right document from the right source to inform executive leadership and board members on the importance of addressing insider threats; and
- It provides a great set of references – good resources for informing an effective program to address insider threat.
First, Consider the Insider
The paper describes the characteristics of “an Insider at Risk of Becoming a Threat” – characteristics recognized by executive leadership. The characteristics of a troubled employee – for example, rebellious or passive / aggressive activity; low tolerance for criticism – may lead to difficulties in a number of ways including a cyber incident.
The paper then identifies “Behavioral Indicators of Malicious Threat Activity” – indicators including an employee interest in areas outside the scope of their responsibility or an employee accessing the network at odd hours or while on vacation or sick leave. Monitoring employee activity is an important part of identifying potential threats.
Then, Detect and Deter
The paper identifies technologies for detection and deterrence. Technologies include data-centric security: data/file encryption, data access control /monitoring, and data loss prevention; intrusion detection / prevention systems; and enterprise identity / access management. The paper helps make the case for the use of the technologies.
The paper also describes the social science behind deterrence strategies – strategies equally applicable to fraud, cybersecurity, and other bad behavior.
Finally, References and Resources
The paper cites 32 references, 29 with online links. I strongly recommend downloading the paper and perusing the links for those that might enhance your insider threat program.
It starts with a link to the Carnegie Mellon CERT Insider Threat web site.
Coordinated Response
This paper focuses on how to Deter and Detect insider threats. We focus on the Coordinated Response to an insider incident. We can help make the case to executive leadership on building an effective insider threat program.
Let us help you with a response plan review that considers your information security risk assessment.
Insider Threat – Webinar
Insider Threats: Learn How to Find them Early and Fix Them Fast!
Your organization has a 50% likelihood of experiencing an insider incident despite deep investments in IT security. Insider threats include fraud, theft of intellectual property, data breaches and leaks, or malicious damage to IT resources. Most organizations that experienced an insider incident indicate it was more damaging than incidents involving hackers. You need the right plan and the right tools to detect, respond and recover from an insider incident.
Join Us on June 5th at 2 PM EDT
Join Mike Tierney, the COO of SpectorSoft and Jim Meyer, Managing Director at Coordinated Response on June 5 at 2 PM EDT for this 60 minute webinar hosted by Dark Reading.
Attend this webinar to learn:
- Effective approaches to detect and address insider threats.
- Research and resources from industry experts to help you prepare and react.
- Best practices from years of hands-on experience and client engagements.
Verizon data breach investigations report indicates that any breach, insider or otherwise, if found early is 80% less likely to result in damage. Register for this webinar and learn how to find insider threats early and fix them fast.
Watch this webinar on YouTube
To see a replay of this webinar go to YouTube.
Adjust the Incident Response Plan – Address Insider Threats
An effective incident response plan addresses the nature of insider threats and includes a range of specialized response actions.
This is the second note on Insider Threats reflecting the Common Sense Guide to Mitigating Insider Threats, 4th Edition, CMU/SEI-2012-TR-012, December 2012. The first note, Insider Threat and Incident Response, summarized key elements of the guide related to incident response planning and management. This note applies those elements to the incident response planning process.
The guide identifies the following items and practices of special importance to incident response when dealing with an insider threat:
- A wide range of organizational staff support the response to an insider threat.
- Consistent enforcement of documented policies and controls support defensible actions.
- A comprehensive employee termination procedure mitigates the risk of insider threats.
- Know and document your assets.
- Consider insider threats in an enterprise-wide risk assessment.
According to the 2012 Cybersecurity Watch Survey a company has a 50% chance of experiencing an insider incident in any given year or a certainty of experiencing an incident in a 2 year time frame (see Insider Threat and Incident Response for specific references). Our note, A Data Breach and Insider Threats, examines the cost of a data breach and the potential roles played by insiders.
The response to an insider incident involves a wide range of organizational staff.
In our Response Management Framework we describe this as the Core and Extended Response Team.
An insider incident is likely to involve legal, human resources, and physical security. More importantly, the actions require special authorizations and notifications as the response proceeds. Using an agile approach – iterating through incident actions with the extended team members – provides a useful delineation of the appropriate actions.
Consistent enforcement of documented policies and controls support defensible actions.
Documented policies that are consistently enforced support defensible actions including employee or contractor termination. Documentation and consistent enforcement are even more important when stronger legal remedies apply. The incident response plan with its associated actions is a key element for documenting policies and for insuring consistent actions.
A comprehensive employee termination procedure mitigates the risk of insider threats.
The Common Sense Guide recommends developing a comprehensive, enterprise-wide checklist to use at the time of separation. The checklist might identify: (1) a list of employees who need to know of the termination; (2) a list of accounts assigned to the employee; and (3) a list of resources to monitor after the termination.
The last point recognizes that terminating an employee may result in escalating the threat presented by the employee. Monitoring key resource post-termination may identify an incident before a serious impact occurs. The checklist can be used to help identify likely insider incidents.
It is important to note that when any insider incident occurs, the incident response may collect important documentation needed to support the termination process.
Know and document your assets.
The guide recommends maintaining an up-to-date inventory of (1) all data types being processed; (2) all devices including network devices, mobile devices, and credentialing tools; and (3) your information geography: sensitive areas; single or multiple locations; domestic or foreign locations; and physical or virtual (cloud-based) locations.
These inventories are important tools needed for all effective incident response, not just insider incidents. Understanding your assets is a critical element of the next practice: an enterprise-wide risk assessment.
Consider insider threats in enterprise-wide risk assessments.
The guide recommends a number of controls that mitigate the risk of an insider threat, for example, background checks. But, the enterprise-wide risk assessment does more. It considers the risk insider threats pose against assets beyond information resources. It provides potential impact assessments associated with various assets. This information is important to building and effective incident response program.
In an earlier note, Risk Assessment and Incident Response, we talk about this important linkage.
Coordinated Response
A coordinated response is a bigger challenge when an incident involves an insider. Establishing en effective plan is an important step and the Common Sense Guide provides elements and practices to hone the perfect plan.
Let us help you with a response plan review that considers your exposure to insider threats.
A Data Breach and Insider Threats
Insiders pose a unique threat. A Data breach involves legal issues. Does your incident response plan reflect the required actions?
The Verizon 2013 Data Breach Investigations Report provides insight into the role of insiders when data is breached.
Profit-driven organized crime groups were tied to over half of all breaches.
Attackers targeted mostly finance, retail, and food service industries. Attackers profit from selling payment data or personal information. Almost all states and the District of Columbia have data breach laws governing this type of incident.
State-affiliated Actors were linked to 21% of all breaches.
Here the attackers were seeking intellectual property – trade secrets, sensitive internal data, or systems information. The targeted industries were Manufacturing, Professional Services and Transportation. This raises issues of liability or economic loss.
There are two important statistics associated with cyber-espionage campaigns.
- First, over 95% started with a phishing attack. Companies need to take their anti-phishing controls seriously.
- Second, smaller companies, those with less than 10,000 employees, were attacked 4 times more than larger companies. Small professional services or law firms were often targets due to the sensitive information they held for their clients.
Malicious Insiders account for 14% of data breaches.
But, Verizon also states that External Actors are involved in over 90% of all data breaches. So, often an external actor recruits or coerces an insider.
Risk Awareness is the first step.
Include insider threats and the potential impact of a data breach in your risk assessment.
An Incident Response Plan is the second step.
When dealing with insider threats, consider the legal and human resource issues. Managing employees or contractors involves legal and regulatory issues. When dealing with a data breach, appropriate legal steps need to be followed.
Coordinated Response
Coordinated Response can help you develop a plan that anticipates the unique actions needed to address a data breach or an insider threat.
Insider Threats and Incident Response
Insider Threats place added requirements on an incident response plan.
In December 2012, The CERT/CC Insider Threat Center published the Common Sense Guide to Mitigating Insider Threats, 4th Edition, CMU/SEI-2012-TR-012. The guide uses extensive research to examine the nature of insider threats and their probability. It is an excellent resource.
This is the first in a series of notes on insider threats – the first note examines the guide and the next considers the impact on incident response planning and handling.
The response to insider threats often involves a wide range of organizational staff.
“Insider threats are influenced by a combination of technical, behavioral, and organizational issues” (from the Executive Summary). As a result, management,human resources (HR), legal counsel, and physical security may be involved in the response along with the Information Technology (IT) and Information Assurance (IA) departments.
Of course, this aligns with the Core and Extended Response Team in the Response Management Framework.
Insiders reflect a range of company relationships and behaviors.
The range includes:
- The traditional threat posed by current or former employees;
- Collusion with outsiders – employees recruited or coerced by competitors or organized crime;
- Business partners – suppliers, contractors, or distribution channels;
- Mergers and acquisitions introducing new, unknown insiders; and
- Cultural issues – both national and corporate – introducing tensions.
Each of these may require specialized incident actions as part of the response.
The 2011 CyberSecurity Watch Survey informs the guide.
The CyberSecurity Watch Survey provides the following statistics:
- 43% of respondents experienced a malicious, deliberate insider incident in the past 12 months.
- 23% of identified perpetrators were insiders – 1 in 4 incidents perpetrated by insiders.
- 46% of respondents felt insider incidents caused more damage than incidents perpetrated by outsiders.
This annual survey is sponsored by U.S. Secret Service, CERT Insider Threat Center, Deloitte, and CSO Magazine.
The 2012 CyberSecurity Watch Survey provides additional support.
The following chart suggests that all organizations – large and small – have close to a 50/50 chance of experiencing an insider incident in any given year. Or every 2 years give or take a month an insider incident will occur. NOTE: there were 479 respondents, 1/3 were organizations with 5,000 employees or more, 2/5 were organizations with less than 500. This suggests a representative survey.
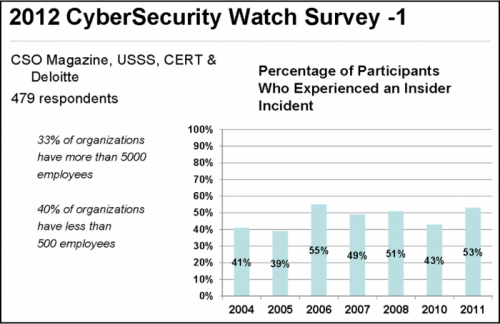 |
||
| The 2012 Survey was retrieved from a Google search for “2012 CyberSecurity Watch”. |
The guide recommends 19 practices to mitigate insider threats.
The guide recommends 19 practices for mitigating Insider Threats (See the table at the end of this article). Many of these are well known security controls, but they are presented through the lens of the insider threat. For each practice, the guide (1) defines the protective measure; (2) identifies challenges; (3) provides case studies; (4) identifies quick wins applicable to all organizations; (5) identifies additional quick wins for large organizations; and (6) maps the recommend practices to NIST, CERT, and ISO standards.
Coordinated Response – Review your plan.
We can work with you to incorporate or improve how your response plan addresses insider incidents.
The 19 Practices for Mitigating Insider Threats.
Emphasized practices have a direct bearing on incident response planning and management.
| 1 | Include insider threats in an enterprise-wide risk assessment. | 11 | Institutionalize system change controls. |
| 2 | Clearly document and consistently enforce policies and controls. | 12 | Log, monitor, and audit insider actions with log correlation or SIEM system. |
| 3 | Incorporate insider threat security training for all employees. | 13 | Monitor and control remote access including mobile devices. |
| 4 | Beginning with the hiring process, monitor suspicious or disruptive behavior. | 14 | Develop a comprehensive employee termination procedure. |
| 5 | Anticipate and manage negative issues in the work environment. | 15 | Implement secure backup and recover processes. |
| 6 | Know your assets. | 16 | Develop a formalized insider threat program. |
| 7 | Implement strict password and account management policies and practices. | 17 | Establish a normal network behavior baseline. |
| 8 | Enforce separation of duties and least privilege. | 18 | Be especially vigilant regarding social media. |
| 9 | Define explicit security agreements for any cloud services – address access restrictions and monitoring capabilities. | 19 | Close the doors to unauthorized data exfiltration. |
| 10 | Institute access controls and monitoring on privileged users. |
From the SEI/CMU Common Sense Guide for Mitigating Insider Threats, 4th Edition.

