Coordinated Response
Services and tools for incident response management
Incident Response Plan
Preparing for an Insider Threat
Join Us in October at the ISACA North America CSX to Learn More.
Your organization has a 50% likelihood of experiencing an insider incident despite deep investments in IT security. Insider threats include fraud, theft of intellectual property, data breaches and leaks, or malicious damage to IT resources. Most organizations that experienced an insider incident indicate it was more damaging than incidents involving hackers. You need the right plan and the right tools to detect, respond and recover from an insider incident.
Business Value
Verizon data breach investigations report indicates that any breach, insider or otherwise, if found early is 80% less likely to result in damage. Join us at the ISACA North America CSX to learn how to detect and respond to an insider incident.
North American CACS
This presentation complements the one we delivered in May at the ISACA North America CACS in New Orleans: “Preparing for a Data Breach.”
Senior Executive Involvement in Data Breach Response
The Ponemon Institute conducted a survey of 495 senior executives both in the United States and the United Kingdom. The findings identify the importance of executive involvement in an effective data breach response.
Key Findings
The following ingredients really apply to any organization evaluating their data security posture, not just law firms.
- Poor communications, lack of leadership and lack of board oversight are barriers to effective incident response.
- Current incident response plans are more reactive than proactive.
- Executive level oversight is critical to minimizing financial loss and protecting reputation and brand.
- Understanding the risk and approving incident response plans should be on the board of directors’ agenda.
- Negligent and malicious insiders are considered the biggest security risk.
This strongly suggests that senior executives need to be involved in the development and review of your incident response plan.
In one recent engagement, we developed and exercised an organization’s incident response plan. Senior executives were directly involved including the COO, two vice presidents of key business units, the chief risk officer, the CIO, and deputy legal counsel. Our client gained from this effort and so did we.
Coordinated Response
Let us help your organization develop, improve, and test your incident response capabilities.
The full study, “The Importance of Executive Involvement in Data Breach Response, (May 2015) is available at this link:
http://www.ponemon.org/blog/the-importance-of-senior-executive-involvement-in-breach-response
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
6 Key Ingredients to a Law Firm Data Security Plan
Jeff Norris, Senior Director of IT Security for Lexis/Nexis Managed Technology Services identified 6 Key Ingredients to a Law Firm Data Security Plan on the Lexis/Nexis Business of Law web site (May 2015). An incident response plan was one of those ingredients.
Data Security Key Ingredients
The following ingredients really apply to any organization evaluating their data security posture, not just law firms.
- Clear Policy and Training Plan.
- Accurate Inventory.
- Access Controls.
- Keep Software Updated.
- Review Liability Coverage.
- Plan for Incident Response.
The first 4 ingredients are about Protect – protecting your data. The last 2 ingredients are about Respond – responding to a cybersecurity incident. This is a clear recognition of the likelihood of an incident.
Coordinated Response
Let us help your organization develop, improve, and test your incident response capabilities.
The full article by Daryn Teague (May 2015) is available at this link:
http://businessoflawblog.com/2015/05/law-firm-data-security/
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
CFOs Need to Focus on Cybersecurity Risk
Incident Response – Executive Awareness.
An article on CFO.COM by Jeffrey Burchill, identifies cybersecurity risks associated with suppliers, service providers, and insiders.
Mr. Burchill, a CFO in the insurance industry, makes the case for CFO involvement in reviewing suppliers and service providers for potential cybersecurity vulnerabilities and risks. He raises a warning about the potential threat posed by insiders, malicious or inadvertent but still a threat.
Clearly, this article speaks to the CFO.
The article is available at: http://ww2.cfo.com/cyber-security-technology/2015/07/cfos-cybersecurity-risk-like-iceberg/
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
Board of Directors – Responsibility for Cyber Risk
Incident Response – Executive Awareness.
A post on the Fredrikson & Byron law firm’s website identified: 4 Legal Considerations to Help Directors Manage Cyber Risk (Evan C. Berquist, September 2015).
Summary
“The United States Court of Appeals for the Third Circuit held that the Federal Trade Commission (FTC) has authority under Section 5 of the FTC Act to regulate cybersecurity.”
“The opinion is the latest development in a legal drama that began after Wyndham Worldwide Corp. (Wyndham) suffered three data breaches between 2008 and 2009. The breaches resulted in the improper disclosure of the personal information of more than 610,000 Wyndham customers.”
“The Wyndham litigation has underscored at least two significant new developments in cybersecurity: First: directors can be held individually liable for their failure to adequately manage cyber risks; and Second: government regulators, including the FTC, the Securities and Exchange Commission (SEC), among others, are making cybersecurity an increasingly important enforcement priority. And courts are ratifying the agencies’ broad assertion of regulatory authority.”
The article is available at: http://www.fredlaw.com/news__media/2015/09/09/995/4_key_legal_considerations_to_help_directors_manage_cyber_risks
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness/
A Legal Perspective on Cyber Incident Response
Incident Response – Executive Awareness.
The law firm of Baker Hostetler often assists clients in responding to cybersecurity incidents. The firm publishes an annual report: Data Security Incident Response Report 2015.
Summary
The 2015 report provides statistics on incidents by industry, a list of probable causes, descriptions of the adverse outcomes, and valuable recommendations. It provides executives with a sense of the risks and potential impacts.
The top 5 causes of incidents experienced by the firm:
- Employee negligence,
- External theft of a device,
- Employee theft,
- Phishing, and
- Malware.
Every company is at risk from these attacks.
The law firm identifies seven proactive steps to be “compromise ready”. The first step is to develop and exercise an incident response plan. The second step is to engage an experienced security consultant to conduct a security assessment. Coordinated Response is well qualified to help with these steps and more.
The full article is available as a PDF file at:
https://www.bakerlaw.com/files/uploads/Documents/Data%20Breach%20documents/BakerHostetler-Data-Security-Incident-Response-Report-2015.pdf
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is one in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
The Economist Urges Response Plan Development
Incident Response – Executive Awareness.
The Economist Intelligence Unit offers a valuable report for raising executive awareness:
Cyber Incident Response – Are Executives Ready?
Summary
This report makes a strong argument for incident response programs (Economist Intelligence Unit 2014). The Economist is recognized by most executives as high value information written with the executive in mind.
The Economist surveyed 360 senior executives. The key findings supported by the survey include:
· The frequency of cybersecurity incidents is on the rise.
· The emphasis on incident response is driving the formalization of plans and processes.
Despite the recommendations, nearly 40% of the respondents failed to plan and 35% lacked a formal response team. We can help address this.
The report is available on the Economist website:
http://www.economistinsights.com/technology-innovation/analysis/cyber-incident-response
Cyber Incident Response – Executive Awareness
Raising executive awareness on the importance of incident response planning should raise executive support. This is the first in a series of references that serve as tools for engaging your executives and gaining their support.
The full collection of references is available at this link:
https://coordinatedresponse.com/topics/incident-response-plan/executive-awareness//
Incident Response – Why Plan
Why not? Planning is a best practice and good business. Besides, it is often a legal or regualtory requirement.
A cybersecurity incident response plan is considered to be 1 of the top 20 security controls by a number of respected authorities. Industry research indicates an effective response to a cybersecurity incident reduces the actual cost by 11%. Developing an incident response plan is not only a best practice, it is good business. See References and Research at the end of this page.
NOTE: This highlight is available as either a Document or a Presentation as a PDF file. See links at the bottom of this page.
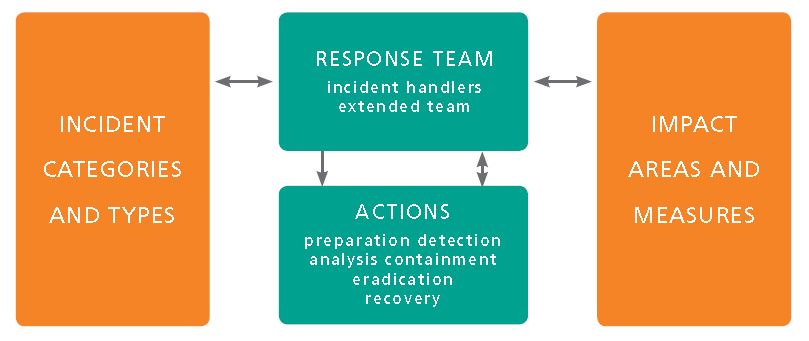
Four Dimensions of Incident Response
A good plan addresses four key dimensions of incident response:
- Scope: identify incident categories and types addressed by the plan.
For example, a plan may address malware, compromised assets (including breached data), and lost equipment or credentials. - Team: start with the core individuals responsible for handling the incident; add extended team members required in select situations, for example, human resources or legal; identify third parties who support the response, for example, an Internet Service Provider or a forensics firm.
- Impact & priority: identify impact areas that might be effected by an incident, for example, financial, reputational, and legal; identify impact levels or measures for each of these areas; this supports setting appropriate incident impact; and this should align with enterprise risk assessments.
- Response actions: for each category and type, identify actions for responding to the incident. For example, examining log files, requesting a legal review, or involving a consultant.
The elements of the 4 dimensions interact throughout the incident response. The response team identifies the likely incident category and type. This informs their action plan. As they execute the plan, information is collected and analyzed. Impact is measured to establish the priorities and communicate with management. Additional resources and actions are invoked as needed and as authorized. Ultimately, the incident is contained and the cause is eradicated. Finally, the organization benefits from the lessons learned.
The Incident Planning Process
The incident planning process starts with the template reflecting the 4 dimensions. An iterative approach is used to interview team members, solicit their input, and build out the plan. The plan is distributed to the team. After review, 1 or more group meetings are held to discuss the plan. Then a final draft is prepared for review and approval.
The planning process serves a number of key objectives.
Develop the plan – first and foremost, the incident response plan is developed and documented.
Socialize and exercise – the planning process “socializes” the incident response plan as well as the roles and responsibilities of the response team members. Team members learn from the planning process. The interviews and group sessions exercise the plan. Team members working together consider “what if” different events or outcomes occur.
Gap analysis – the planning process often identifies short comings in the response capability. Filling the gaps might be as straight forward as training team members or acquiring equipment needed for response. Filling the gaps may also require working with service providers to acquire additional resources when needed.
Reference and Research
National Institute for Standards and Technology
National Institute of Standards and Technology (NIST)Special Publication SP 800-53 Rev 4, Security and Privacy Controls for Federal Information Systems and Organizations, identifies Incident Response (IR) as 1 of the 18 families of information security controls:
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf.
NIST also provides SP 800-61 Rev 2: Computer Security Incident Handling Guide, August 2012 to help organizations develop their incident response program:
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf.
International Standards Organization
The International Standards Organization defines ISO 27035:2011 as the standard for Information Security Incident Management: http://www.iso.org/iso/catalogue_detail?csnumber=44379.
Ponemon Institute
Ponemon Institute performs an annual survey of organizations that experienced a data breach in the past year. The survey is global, but the numbers provided here are for the United States. The survey included 62 companies, across 16 industries.
- $217 – the average cost per compromised record.
- $259 – the average cost per compromised record in the financial institutions.
- $6.5 million – the average total cost.
- 11% – cost reduction realized by organizations with an incident response program.
- $715,000 – the average savings realized by organizations with an incident response program.
Ponemon Institute, 2015 Cost of a Data Breach: United States, May 2015, sponsored by IBM.
Retrieved 08/15/2015 from: http://www-03.ibm.com/security/data-breach/.
Why Plan – Document and Presentation
https://coordinatedresponse.com/wp-content/uploads/2015/08/Why-Plan-Document.pdf
https://coordinatedresponse.com/wp-content/uploads/2015/08/Why-Plan-Presentation.pdf
For more information refer to our Response Management Framework.
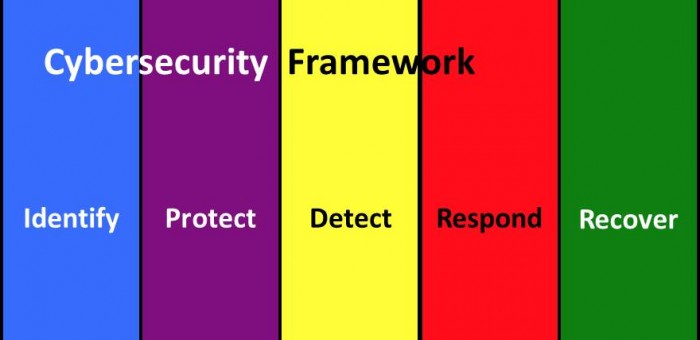
NIST Cybersecurity Framework – Respond and Recover
The NIST Cybersecurity Framework identifies five cybersecurity functions. Two of the functions are Respond and Recover.
Separating Recovery from Incident Response
Working with our clients, we see Recovery as separate from Incident Response. The National Institute for Standards and Technology (NIST) Cybersecurity Framework confirms that view: Respond and Recover are separate functions.
Recovery might involve a wide range of activities from restoring a data set or a system to pursuing legal action to recover damages. These activities are the province of specific organizational elements well beyond the scope of incident response. Recovering a data set or a system is likely the responsibility of an operational unit in the information systems organization. This unit recovers components impacted for many reasons, not just cyber incidents.
The Incident Response team might initiate the recovery process, but the incident is often closed before recovery is complete.
Earlier NIST Guidance
In SP 800-61 Rev 2 Computer Security Incident Handling Guide, 2012, NIST identified 4 phases for incident response. The third phase includes Contain, Eradicate, and Recover. Thus, treating Recover as an integral part of the response effort.
For a copy of the incident handling guide use the following link:
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Incident Response Plan
Whether or not your organization includes Recovery as part of Incident Response the relationship between Respond and Recover needs to be defined in the Incident Response Plan.
Penn State and a Coordinated Response
Penn State was hacked, but returned “a coordinated and deliberate response.”
NOTE: Our firm, Coordinated Response was NOT involved, but we can all learn from Penn State’s response. The response includes a number of best practices highlighted in this article.
On May 15, 2015 Penn State announced the discovery of two sophisticated cyber attacks. “In a coordinated and deliberate response by Penn State, the College of Engineering’s computer network has been disconnected from the Internet and a large-scale operation to securely recover all systems is underway.”
For more details read the announcement on the Penn State web site, but here are some best practices.
An Effective Communications Plan
Penn State announced the breach on May 15. On the same day, they released the web site http://securepennstate.psu.edu/ to keep students and faculty informed of events. The URL suggests they were prepared for any eventuality. Penn State also notified research partners and individuals who may have had sensitive data exposed to the intruder.
Detect and Analyze
On November 21, 2014, the FBI alerted Penn State of a cyber attack with unknown origins and scope. The University’s security experts along with outside experts began an extensive investigation. Mandiant, a FireEye company, was one of the experts. The investigation determined that the earliest confirmed date of intrusion was September 2012 — over 2 years earlier.
Contain: Protect and Preserve
Steps were immediately taken to further protect and preserve critical information and sensitive data on the College of Engineering Systems.
Cone of Silence
No announcements were made to avoid alerting the intruder and to avoid unwanted damage or destruction.
Eradicate and Recover
On May 15, once the scope and nature of the intrusion were known, the engineering systems were taken offline to remove malware, secure the systems, and restore them to operational status. This is expected to take several days. All passwords are being reset to address potentially compromised credentials.
Communicate
Once the investigation was completed the communication plan was launched.
Lessons Learned
Two factor authentication for remote access to the Engineering systems is being implemented now. This will be extended to the rest of the University later this year. Additional measures were taken to improve the security posture.
Coordinated Response
One might question why it took over 2 years and an outside organization to discover the intrusion. But, experience suggests state actors operate “slow and low”. First, the intruders observe without leaving “foot prints” for an extended period. Then, instead of leaving 10 foot prints a day, they leave 1 a day for 10 days. They work hard to make it hard to detect.
But, once alerted, Penn State responded with a well planned and well coordinated response. Let us help your organization with an incident response plan review. Together, we can apply best practices to improve the plan and the outcome of a cyber incident.