Coordinated Response
Services and tools for incident response management
Impact Assessment
A Data Breach and Insider Threats
Insiders pose a unique threat. A Data breach involves legal issues. Does your incident response plan reflect the required actions?
The Verizon 2013 Data Breach Investigations Report provides insight into the role of insiders when data is breached.
Profit-driven organized crime groups were tied to over half of all breaches.
Attackers targeted mostly finance, retail, and food service industries. Attackers profit from selling payment data or personal information. Almost all states and the District of Columbia have data breach laws governing this type of incident.
State-affiliated Actors were linked to 21% of all breaches.
Here the attackers were seeking intellectual property – trade secrets, sensitive internal data, or systems information. The targeted industries were Manufacturing, Professional Services and Transportation. This raises issues of liability or economic loss.
There are two important statistics associated with cyber-espionage campaigns.
- First, over 95% started with a phishing attack. Companies need to take their anti-phishing controls seriously.
- Second, smaller companies, those with less than 10,000 employees, were attacked 4 times more than larger companies. Small professional services or law firms were often targets due to the sensitive information they held for their clients.
Malicious Insiders account for 14% of data breaches.
But, Verizon also states that External Actors are involved in over 90% of all data breaches. So, often an external actor recruits or coerces an insider.
Risk Awareness is the first step.
Include insider threats and the potential impact of a data breach in your risk assessment.
An Incident Response Plan is the second step.
When dealing with insider threats, consider the legal and human resource issues. Managing employees or contractors involves legal and regulatory issues. When dealing with a data breach, appropriate legal steps need to be followed.
Coordinated Response
Coordinated Response can help you develop a plan that anticipates the unique actions needed to address a data breach or an insider threat.
ISACA Incident Management and Response
ISACA – The Information Systems Audit and Control Association – is a good resource for Incident Response Teams.
The ISACA Web Site offers a white paper: Incident Management and Response. This is a link to the base page with access to the white paper as well as a good set of additional resources for Incident Planning and Response.
The paper makes key points that help strengthen a response plan including:
- The importance of the link between risk planning and response planning;
- The business value of a good response plan; and
- The importance of supporting enterprise governance in the response plan.
Attacks Expose the Enterprise to a Variety of Risks and Associated Impacts
Risk planning and response planning are linked. The risks and resulting impacts occur in the following areas:
- Reputational Risks including public relations or legal issues with customers.
- Regulatory Risks including the inability to meet regulatory compliance.
- Operational Risks including the inability to deliver key business capabilities.
- Internal, Human Relations Risks including inability to process payroll or violations of employee privacy.
- Financial Risks including loss of physical assets or remediation expenses.
This is an idea that Coordinated Response embraces in The Risk Management Framework specifically in the area of Impact Assessment and Incident Prioritization.
Business Value – An Effective Response Plan Addresses Response Risk
A robust incident response program reduces the risk of response – the probability of the response itself contributing inadvertently to risk exposure. The paper stresses the characteristics of an effective program:
- Is the plan endorsed by management?
- Is the team well-trained?
- Is the team interdisciplinary? Does the team include operational, administrative, legal, HR, PR, and management?
- Does the program employ proven plans and processes for operations and execution?
- Are metrics employed for evaluating effectiveness and identifying gaps?
- Is there a charter for the team?
- Does the plan address declaration and notification procedures? A well defined communication plan?
Impact Levels
For each impact area, it is important to provide metrics or descriptions that differentiate the impact level. Low, medium, and high are not enough as impact measures. Without metrics different people assign different meanings to the terms low, medium, and high.
An Incident Response Plan Review
It’s worth stressing that the impact component of the risk assessment can and should be used during the Incident Impact Assessment. The Response Team measures adverse impact to determine the needed response.
With this information the response team makes informed decisions on what resources to apply and what actions to take. Refer to our Response Management Framework for added insight.
Let us help you with a response plan review that considers your information security risk assessment.
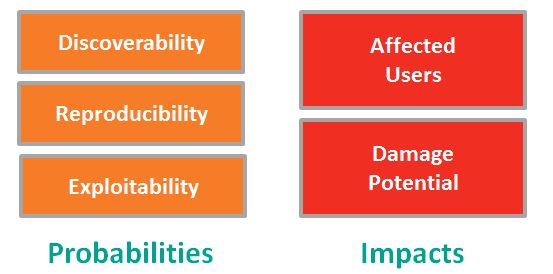
Threat and Impact Assessment with DREAD
DREAD – Damage Potential, Reproducibility, Exploitability, Affected Users, and Discoverability – is used to quantify risk, but it may prove useful for incident impact assessment.
DREAD is a classification scheme for quantifying, comparing, and prioritizing the amount of risk represented by a specific threat. The DREAD scheme is described in Writing Secure Code, 2nd Edition, Howard, M. and LeBlanc, D. Microsoft Press 2003 and is used by Microsoft. DREAD is also promoted by the Open Web Application Security Project (OWASP) on their site: Threat Risk Modeling.
In the diagram above and in the definitions below, the “D”s are reordered to group the elements of DREAD into logical categories: Probabilities and Impacts.
Threat Probabilities:
How easy is it to (1) Discover a vulnerability, (2) Exploit a vulnerability, and (3) Reproduce the Exploit? In DREAD these are rated on a scale of 0 (very hard or impossible) to 10 (easy with limited tools or skills).
Threat Impacts:
Affected Users are measured from 0 (none) to 5 (Some users, but not all) to 10 (all users). Damage Potential is measured from 0 (no damage from exploit) to 5 (individual user data is compromised) or 10 (complete system or data destruction or compromise).
Risk Measure:
Add the 5 metrics and divide by 5. The result is a scale of 0 (not likely with limited impact) to 10 (highly likely with serious impact). Obviously, higher risk requires additional mitigation or avoidance might be required.
Incident Response and Risk Assessment
It’s worth stressing that the impact component of the risk assessment can and should be used during the Incident Impact Assessment. The Response Team needs to know how many users are affected, how much data or how many systems have been compromised, destroyed or disabled.
With this information the response team makes informed decisions on what resources to apply and what actions to take.
In an Incident postmortem review, the questions about the vulnerability should be reviewed: discoverability, reproducibility, and exploitability (again).
NIST Incident Impact Assessment – Revised
NIST Revised their guidance on Incident Impact Assessment in The Computer Security Incident Handling Guide, SP 800-61 Revision 2, August 2012.
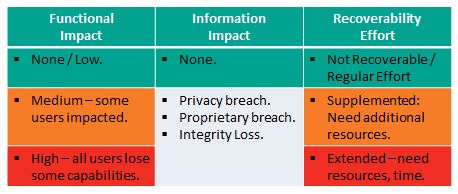
Revision 1 provided a complex measure for incident impact assessment that might provide insight in hindsight, but one that was not practical, applicable, or useful in the midst of an incident response. The new measures, suggested in the table above, are really quite useful, applicable, and discernible. There are 3 important impact areas with associated metrics:
- Functional impact
- Information Impact
- Recoverability Effort
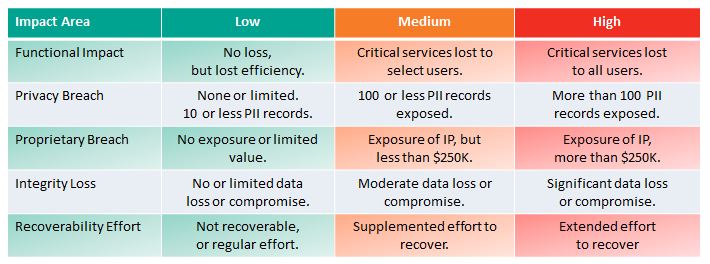
Functional Impact
This measures loss of system functionality. NONE – No loss of functionality. LOW – no loss of functionality, but loss of efficiency. MEDIUM – Critical services lost to a subset of users. HIGH – Critical services lost to all users.
Information Impact
Here NIST stops short of measuring impact – so the above diagram is not colored for this Impact Area except in the case of NONE – no information was exfiltrated, modified, or deleted. An impact measure is needed for each of the three information impact areas. PRIVACY BREACH – personally identifiable information was compromised. PROPRIETARY BREACH – unclassified proprietary data was compromised. INTEGRITY LOSS – sensitive or proprietary information was changed or deleted. A level of impact measure is needed in each of these areas. The loss of a single document or individual’s data is low, but what defines medium or high?
Recover-ability Effort
This is an interesting and useful metric: Is the data/system recoverable? If so, what is the level of recovery effort? NOT RECOVERABLE – the data or system cannot be recovered. REGULAR – time-to-recover is predicable with existing resources. SUPPLEMENTED – time-to-recover is predictable, but with additional resources. EXTENDED – time-to-recover is unpredictable and additional resources including outside help are needed.
Coordinated Response
This new approach agrees with the Coordinated Response Impact Assessment in the Response Management Framework. The table below shows the 5 possible impact areas with associated impact metrics.
Coordinated Response can help you review and improve your Incident Response Plan.
Risk Assessment and Incident Response
Align your Incident Response plan with your information security risk assessment.
An effective risk assessment, regardless of the technique employed, identifies impact areas and potential impact levels. Then, given the probabilities an attack, risk strategies are defined: avoid the risk; mitigate the risk; share the risk; accept remaining risk.
Ultimately, unless you choose to avoid the risk, some residual risk is accepted. Then, when an unlikely incident occurs, an incident response plan is the last line of defense.
Risk Assessment – Incident Response – Impact Assessment
The key to an effective impact assessment rests with two key questions:
• What areas of your business are at risk when an incident occurs?
• How do you measure the impact?
These two questions are first asked during the risk assessment – the theoretical question: what if? When an incident occurs, they are asked again, only it is no longer in theory. What areas of your business are affected? To what level?
Impact Areas
While most organizations evaluate the financial impact, the majority view reputational impact as the more important. Other areas to measure include operational impact and legal impact. If your organization is regulated, you might measure legal impact, policy impact, and regulatory impact as separate areas.
Impact Levels
For each impact area, it is important to provide metrics or descriptions that differentiate the impact level. Low, medium, and high are not enough as impact measures. Without metrics different people assign different meanings to the terms low, medium, and high.
An Incident Response Plan Review
It’s worth stressing that the impact component of the risk assessment can and should be used during the Incident Impact Assessment. The Response Team measures adverse impact to determine the needed response.
With this information the response team makes informed decisions on what resources to apply and what actions to take. Refer to our Response Management Framework for added insight.
Let us help you with a response plan review that considers your information security risk assessment.